It was sometime in April 2013, that I wrote my last blog post. Titled ‘And Then They Came For Us’, or something along those morbid lines, the piece was a commentary of sorts based on tweets, photographs and Facebook updates sent out by friends attending a peaceful vigil at the center of Colombo, when marauding monks disrupted their activity. In the aftermath, as a mini-war broke out online with images of participants shared at a furious rate by the disruptors, accompanied with vicious, inflammatory and inciteful comments, I began the quiet job of dismantling my blog and cleaning out my ‘online footprint’. It was not just that I was disturbed at the way hate spewed forth online; the Government’s increasing interest in the world of the wide web had me convinced it was a matter of time before public example would be made of online activists.
A Panopticon state: We must not wait until they come for us, Roel Raymond
Former Fisheries Minister Rajitha Senaratne, a friend of the Rajapaksa family for more than 40 years, said a core group of party leaders had planned to defect in secret — swapping their telephones for ones they trusted not to be tapped, speaking in code and via group chats on Viber, a mobile app.
For Sri Lankan President, Renounced by Aides, Confidence of Re-election Dims, New York Times, Ellen Barry
Who was The Hacking Team?
As noted on the Wikipedia entry on The Hacking Team, the company is
“… a Milan-based information technology company that sells offensive intrusion and surveillance capabilities to governments and law enforcement agencies. Its remote control systems enable governments to monitor the communications of internet users, decipher their encrypted files and emails, record Skype and other Voice over IP communications, and remotely activate microphones and camera on target computers. The company has been criticized for providing these capabilities to governments with poor human rights records.”
In 2013, Reporters Without Borders warned that The Hacking Team, amongst other similar companies called ‘digital mercenaries’, all sold products used to commit violations of human rights and freedom of information. “If these companies decided to sell to authoritarian regimes, they must have known that their products could be used to spy on journalists, dissidents and netizens”.
In early July, The Hacking Team itself got hacked, and around 400Gb of internal emails were dumped online. This was far too much data to download and sift through especially from Sri Lanka. On 8th July, Wikileaks released more than one million emails from this trove through a web based, searchable portal. This article is based on the email accessed through the Wikileaks portal.
What did The Hacking Team do in Sri Lanka?
Unsurprisingly, The Hacking Team was repeatedly approached by Sri Lanka’s intelligence services for its products and services. On 29th July 2013, a representative of a company called S.W. International wrote to The Hacking Team, requesting a description of their system in order to present it to “Director of the Intelligence Bureau at a personal level”. After being provided the information, on 14 August 2013, it is noted that the meeting with the Director of the Intelligence Bureau was “positive”, but that in 2013, the allocated budget of capital expenditure for the unit was already utilised.
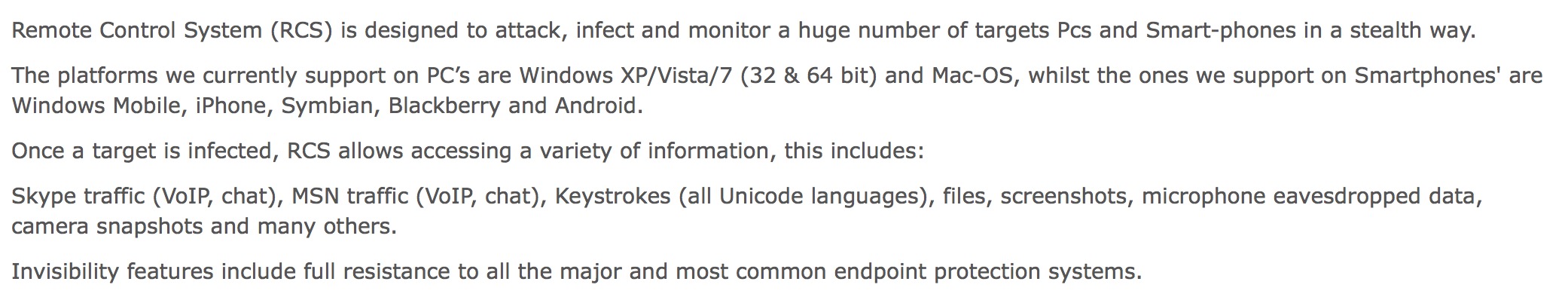
The conversation is around The Hacking Team’s Remote Control System (RCS) product, described in the product brochure as “the hacking suite for governmental interception”. Though final pricing would obviously depend on the exact configuration and services requested, online reports suggest the going price for RCS to be in the region of 48,000 USD ($1,000,000 Birr paid by the Ethiopian government for RCS converted to USD at today’s rates).
The capabilities of RCS are quite remarkable. Taken from an email from The Hacking Team sent in May 2013,
Click the image above for larger version.
Continuing the same email thread over months, in March 2014 it is noted in an email to The Hacking Team that the “Sri Lanka Ministry of Defense is planning to develop a electronic surveillance & tracking system of their own in conjunction with a local university”.
In what is seemingly a parallel discussion, The Hacking Team is approached in November 2014 by the Sri Lankan Police and the CID. The resulting email thread leads to planning a live demo of The Hacking Team’s product(s) in January 2015. Given the events of 8th January, it is unclear whether this live demo actually went ahead.
In what is yet another discussion with The Hacking Team in May 2013, someone who is purportedly a very dear friend of the Director of the National Intelligence Bureau (NIB) (noted, correctly, in the email as Sri Lanka’s equivalent of the CIA) asks the company to provide information on its products and services to “very urgently move forward” with procurement. The Hacking Team’s response is rather interesting: “Can you please confirm that National Intelligence Bureau is a different body from Military Intelligence? It would be helpful if you could describe me to what body NIB reports to.”
What’s even more interesting is the manner in which proxies associated with or brokers working for the Sri Lankan government used dummy corporations to hide the money trail. The most revealing information on this score is the exchange between someone called Huzam Usuph and The Hacking Team, in April 2013. As noted by Usuph,
One of most important things in selling and dealing with Defense sectors in Sri Lanka is I have sold many sensitive technologies and the acquisition has been very confidential to date no media or any one has reported or exposed what interception technologies have been acquired by our intelligence sources.
The pushback from The Hacking Team in dealing with what is clearly noted as a dummy corporation is worth reading. It is unclear whether the deal went ahead.
In addition to digital surveillance technologies, The Hacking Team was also approached to secure military equipment for the for the Commonwealth Heads of Government meeting in October 2013. See here and here. S.W. International keeps cropping up in The Hacking Team’s email records, and it is unclear what relationship this company enjoys with Sri Lanka’s Ministry of Defence in particular, and other arms of the military and Police in general.
Resources
The full tranche of emails containing both the words Sri Lanka can be accessed via Wikileaks here, or as a PDF (200 pages) here. An offline version of the search results can be accessed here (unzip the file and open it using any browser). All of the emails referenced in this article can be accessed from a single page here.
The Centre for Policy Alternatives has produced a range of content to combat growing surveillance and censorship of online content in Sri Lanka. See here.