A team of researchers from the Netherlands' national institute of mathematics and computer science alongside Google have devised the first practical "collision" attack against the widely used SHA-1 cryptographic function.
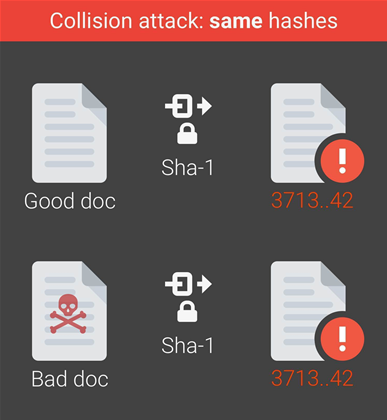
As a proof of concept for the attack, the researchers created two Adobe PDF files with different content, yet have the same SHA-1 digital signature.
They said this could be abused to forge signatures on other documents:
"... by crafting the two colliding PDF files as two rental agreements with different rent, it is possible to trick someone to create a valid signature for a high-rent contract by having him or her sign a low-rent contract," the researchers explained.
While there have been theoretical collision attacks in the past few years, this is the first practical evidence showing SHA-1 can be abused by digital forgeries.
The Secure Hash Algorithm 1 was developed by the United States National Security Agency.
It was released as the US federal information processing standard (FIPS) in 1995, but researchers found theoretical holes in the crypto function some ten years after, suggesting it might not be secure to use against well-funded attackers armed with plenty of computing power.
Due to the weaknesses found in the crypto, SHA-1 was officially deprecated by the US National Insititute of Standards and Technology (NIST) in 2011. Google's Chrome and Mozilla Foundation's Firefox will both warn if SHA-1 digital certificates are being used, starting this year.
But SHA-1 remains widely run, and many different applications rely on the crypto to verify digital signatures, as well as file integrity and identification use cases such as software vendors signing applications.
The GIT open source code repository also uses SHA-1 for identification and integrity checking of all files and code commits, the researchers said.
"It is essentially possible to create two GIT repositories with the same head commit hash and different contents, say a benign source code and a backdoored one.
"An attacker could potentially selectively serve either repository to targeted users," the researchers said.
Nevertheless, cracking SHA-1 still demands a significant amount of money and computational power.
The researchers pointed out this attack - which they have dubbed SHAttered - is 100,000 times faster than using brute force to break SHA-1. A brute force attack would require 12 million years of graphical processing unit calculations to complete, and is impractical they said.
In comparison, the SHAttered attack requires 6500 years of single central processing unit (CPU), or 110 years of single-GPU computations to complete.
Using a p2.16xlarge instance with 16 Nvidia K80 GPUs that cost US$14.40 per hour for 71 device years on Amazon Web Services, the researchers estimated in the paper [pdf] the cost of the attack would be US$560,000 (A$726,000).
This could be lowered to US$110,000 (A$143,000) with a smaller AWS g2.8xlarge instance, with a computational effort of 100 device years at 50 US cents an hour, making the collision attack a possibility for well-funded adversaries, or state-sponsored actors.
SHA-1 with counter-cryptoanalysis hardening is not vulnerable to the attack as it adjusts the computation to produce a safe hash, when it detects a collision, the researchers said.
To further protect against SHA-1 collision, the researchers recommend using stronger crypto alternatives such as SHA-3 and SHA-256.
A tool developed by the researchers to detect SHA-1 collisions is available on Github.



















